DigitalOcean Renews Sponsorship – A Strong Foundation for rsyslog Innovation
We are pleased to announce that DigitalOcean has renewed its sponsorship of the rsyslog project. The partnership between rsyslog and DigitalOcean has been in place for many years and continues to be an essential part of our technical infrastructure.

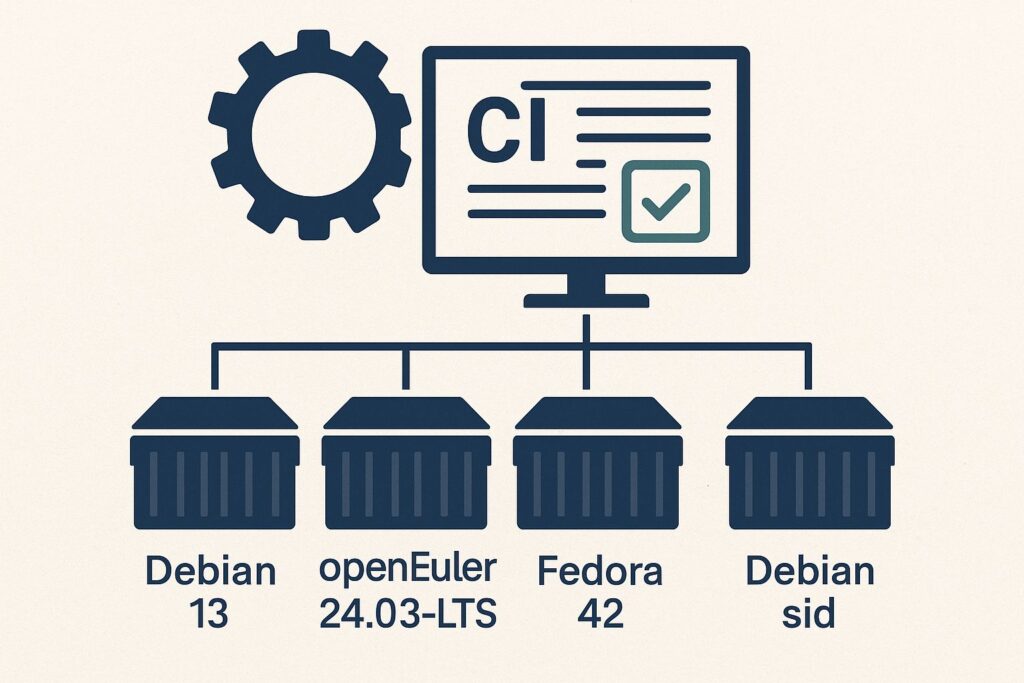
CI extended: Debian 13, openEuler 24.03-LTS, Fedora 42, Debian sid
TL;DR: We added Debian 13, openEuler 24.03-LTS, Fedora 42, and Debian sid to rsyslog CI. We retired Ubuntu 18.04. CI runs use GitHub-hosted runners plus self-hosted workers, with infrastructure sponsored by GitHub, DigitalOcean, opencsv, and Adiscon.
Improved rsyslog Assistant available
We’ve rolled out an update to the rsyslog Assistant, our AI-powered helper for configuration, troubleshooting, and general support. The new release uses an optimized base prompt and updated documentation, leading to better accuracy in first tests.
Continue reading “Improved rsyslog Assistant available”rsyslog status update – what is going on?
There is lots of work going on with rsyslog currently. The last scheduled stable release, v8.2508.0 happened on August , 26th 2025. Be reminded that we offer daily stable releases which enable you to bnefit early from new features and bug fixes.

Rsyslog project update: faster reviews, clearer process
Summary
We are tightening our contribution workflow to improve review speed and predictability. Expect reasonable turnaround times, not instant responses. This is rolling out now.
What changes now
- Initial PR look: Maintainer aims to glance at each new PR within 3 business days.
- AI review on PRs: Runs automatically on open. In our experience it is 90%+ correct and provides actionable items.
- Full review trigger: Deeper maintainer review typically follows when CI is green and AI items are fixed or clearly explained.
- Old issues policy: No mass closures. We are revisiting older items with AI assist and closing them for the right reasons, often by implementing what is needed.
- Labels and dashboards: We are formalizing labels (including good first issue) and lightweight dashboards to make navigation and triage easier. Details will follow in a separate post.
- Responsible AI First: We use AI to speed feedback, but only where it adds real value and the results make sense.
rsyslog 8.2508.0 (2025.08) – release announcement
Download: https://www.rsyslog.com/files/download/rsyslog/rsyslog-8.2508.0.tar.gz
Project-provided packages are building now and are expected later today. Ubuntu PPAs are already done.
We are excited to ship a large and meaningful rsyslog release. This cycle advances our responsible “AI First” strategy and moves decisively toward cloud native operations. It also delivers major quality, security, and documentation improvements.
Continue reading “rsyslog 8.2508.0 (2025.08) – release announcement”New Notification Channels for Rsyslog News
There are now two additional ways to get rsyslog news:
These channels are operated by maintainer Rainer Gerhards. They are meant for people who find it convenient to receive rsyslog updates via messenger platforms.
Continue reading “New Notification Channels for Rsyslog News”Introducing the rsyslog commit AI assistant
We are adding a new helper to our Responsible AI First toolbox: the rsyslog commit (message) assistant. It is an optional ChatGPT Custom GPT that helps contributors write clear, policy-compliant commit messages faster. You stay in full control. Nothing in your workflow changes unless you want it to.
It follows our responsible “AI First” strategy and is optional, transparent, and keeps the human in full control.
- Use it in your browser: https://www.rsyslog.com/tool_rsyslog-commit-assistant
- Review its exact behavior (full transparency):
https://github.com/rsyslog/rsyslog/blob/main/ai/rsyslog_commit_assistant/base_prompt.txt - Discuss and give feedback: https://github.com/rsyslog/rsyslog/discussions
Backticks in RainerScript just got smarter: ${VAR} and adjacent text now work
TL;DR
Backticks with echo in RainerScript now support brace-style environment variables (${VAR}) and adjacent text (e.g., `echo sasl.password=${KAFKA_PASSWORD}`). This removes a common pitfall when assembling key=value pairs for modules like omkafka. It’s still a limited, intentional subset—not a full shell. The change was motivated by real-world confusion reported in issue #5827. (GitHub)
Shipping Better Docs with AI: Restructuring Module Parameters for Clarity and Consistency
As you may know from past articles, we’re in the process of a major documentation overhaul. I wanted to share a focused task we’ve been working on over the past couple of days. This effort highlights our practical, responsible approach to an “AI-First” strategy, where AI is a powerful tool guided by human expertise, not a replacement for it.