rsyslog 8.2602.0: ROSI Collector, rate-limit policies, stronger TLS, and telemetry integration
We have released rsyslog 8.2602.0, the February 2026 scheduled-stable version. Scheduled-stable releases are bi-monthly snapshots of the daily-stable branch, providing predictable update points with the same functional content as daily-stable at the time of the snapshot.
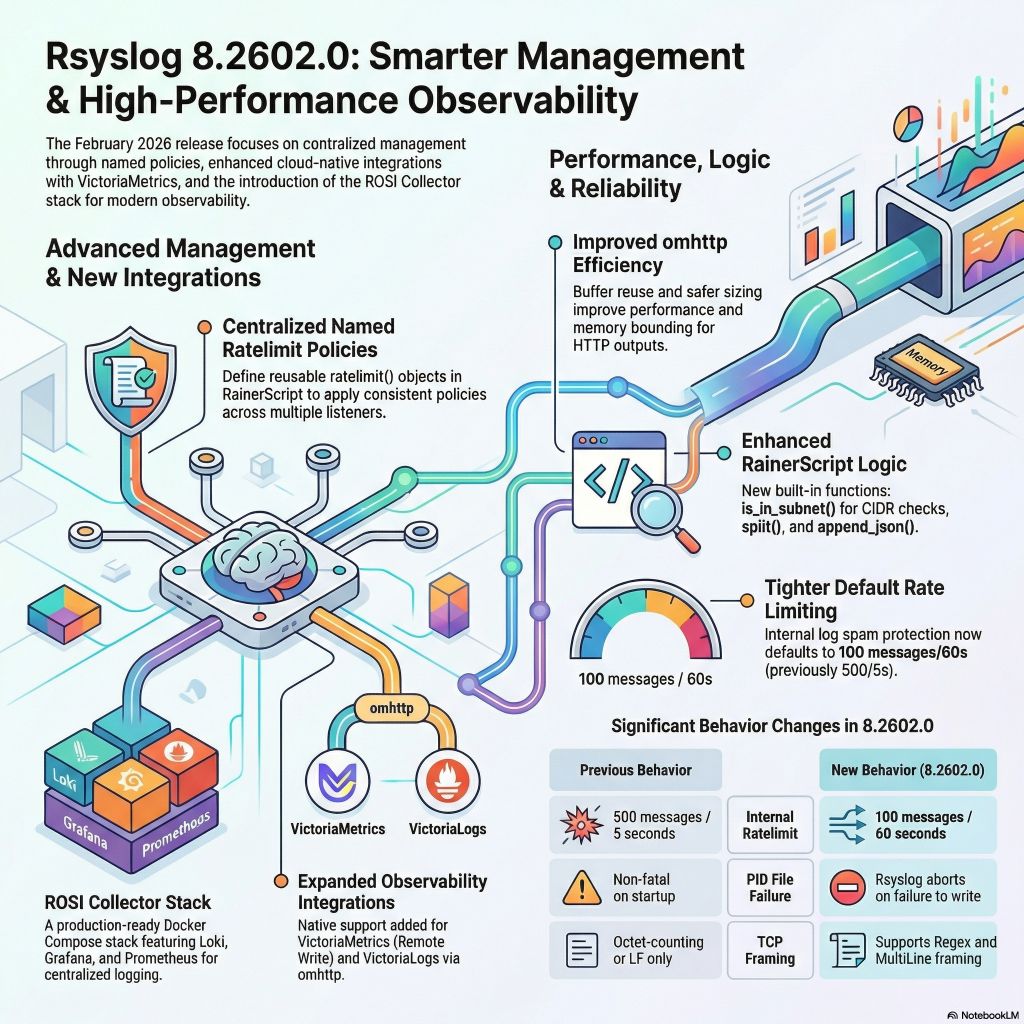
This release introduces a new production-ready deployment stack and continues significant runtime and security hardening.
Four major highlights:
- ROSI Collector: centralized log collection stack
- Named rate limit policies for imtcp and imptcp
- Security and TLS hardening
- Telemetry and ecosystem integration
ROSI Collector: production-ready centralized log collection
This release adds the ROSI Collector (RSyslog Open System for Information), a production-ready Docker Compose stack for centralized log collection and monitoring.
The stack includes:
- rsyslog log receiver
- omhttp output to Grafana Loki
- Grafana Loki (30-day retention)
- Grafana with five pre-built dashboards
- Prometheus for metrics
- Traefik reverse proxy with automatic Let’s Encrypt TLS
- TLS/mTLS syslog reception on port 6514 (RFC 5425)
TLS support features:
- Optional TLS profile via
docker compose --profile tls up -d - Environment-based configuration (ENABLE_TLS, TLS_CA_FILE, etc.)
- Auth modes: anon, x509/certvalid, x509/name
- Certificate generation scripts
- Automatic UFW firewall configuration for port 6514
The stack is included directly in the repository under deploy/docker-compose/rosi-collector/, with dedicated documentation, architecture diagrams, and dashboard screenshots.
Ref: https://github.com/rsyslog/rsyslog/issues/6323
Named rate limit policies
Rate limiting can now be centrally defined and reused.
- Top-level
ratelimit()RainerScript object - Shared policies referenced via
RateLimit.Name - Optional YAML-backed policy files (requires libyaml)
- Thread-safe central registry
Note that there is further work on the rate-limiting capabilities under way.
Default change
The internal rate limiter default is now 500 messages / 5 seconds (previously 100 messages / 60 seconds). This reduces excessive internal log spam during tight error loops.
Security and TLS hardening
- Experimental OCSP certificate revocation checking (disabled by default)
- Fix for potential authorization bypass in nsd_ossl
- Multiple OpenSSL driver fixes (double-free, double-close, memory leaks)
- Improved failed handshake handling
- wolfSSL backend support (build-time selectable)
Note: OCSP requests are currently synchronous and may block threads.
Telemetry and ecosystem integration
- impstats: VictoriaMetrics, via Prometheus Remote Write support
- CI test for VictoriaLogs via omhttp
- impstats atomic overwrite option (
log.file.overwrite), great for Prometheus scraping - a sidecar container process for impstats scraping, with support for older rsyslog versions
- Optional dynstats state persistence
Additional improvements
imtcp
MultiLinesupport (mirrors imptcp capabilities)framing.delimiter.regex- Improved ptcp connect robustness
- Correct worker stack size handling on musl systems
omfwd
- DNS SRV-based discovery via
targetSrv
omhttp
- Safer reply buffer reuse
- New
replymaxbytes(default 1 MiB) - New
healthchecktimedelay - Curl compatibility fixes
Runtime and queue robustness
- Harden disk queue recovery after invalid .qi
- Re-implemented queue size warnings
- Multiple worker lifecycle race condition fixes
- Lookup table reload race fix
- IPv6 DNS cache correction
imfile
- Inode generation check for rotation detection
- Inotify fallback rescans
- State file and file handle fixes
Build and documentation
- Autotools-integrated documentation generation
- Expanded documentation
- Testbench refactoring
- Code coverage targets
- AI workflow and RAG build integration
New dependencies
- libyaml-dev
- libprotobuf-c-dev
- libsnappy-dev
- protobuf-c-compiler
YAML-based rate limit policies require libyaml.
Compatibility notes
- Startup now aborts if the PID file cannot be durably written.
- omhttp
replymaxbytesmay affect retry behavior in edge cases. - YAML policy files require libyaml support at build time.
Thank you
We thank all contributors who made this release possible.
- 20syldev
- Daniel Gollub
- Hayden Roche
- Jan Jeroným Zvánovec
- Janmejay Singh
- Nelson Yen
- n2yen
- Sagar Singh
- shinigami35
- Théo Bertin
- Yuli Fiterman
- @HappyDrink-okk
All other changes were contributed by Adiscon GmbH.
